As your organisation grows it begins to amass more and more data with everything from financial reports, presentations, files, and most importantly, sensitive client and business information. All of this information which represents hundreds of thousands of man-hours could disappear in the event of a disaster. The wrong opened email may invite invasive malware to cause chaos on your business network. The most common reason behind massive data loss remains to be viruses, ransomware and malware; all of which can infiltrate your network.
What is Malware and what does it do?
Malware is short for malicious software. It’s a code, script or software that is specifically designed to damage, encrypt, steal, or perform illegitimate action on devices, data, hosts, or entire networks.
There are many different types of Malware that have varying ways of infecting systems and propagating themselves. You may of heard of WannaCry, Locky, Rapid or Petya recently.
Malware is commonly delivered via an email attachment such as a ZIP file or attached as macros to certain email files or can be downloaded with files from the internet. It cannot damage the physical hardware or network equipment, but it can damage the data and software that resides on them.
The two main types of Malware
Two of the most common types of malware are known as Viruses and Worms. These types of programs are able to self-replicate and can spread copies of themselves. To be classified as a virus or worm, the Malware must have the ability to grow on its own. The main difference between these two is that a worm operates more or less independently of other files, whereas a virus depends on a host program to spread itself. We explore each in more detail below.
Computer Viruses
A computer virus is a type of Malware that propagates by inserting a copy if itself within another program. As with human viruses, a computer virus can easily spread from one computer to another. Viruses can range in severity from causing annoying functionality bugs to damaging data or software and causing denial-of-service (DoS) conditions throughout the network.
Worms
Unlike computer viruses, worms are standalone software and do not require a host program or human help to propagate. A worm enters a computer through a vulnerability in the system setup and takes advantage of file-transport or information-transport features on the system, allowing it to travel around unaided. Like viruses, worms are able to self replicate and can therefore cause the same type of damage.
Is Ransomware a type of Malware?
Yes, Ransomware is a type of Malware that cleverly blocks access to your computer files and quickly spread to other devices on the network. Cyber Criminals encrypt devices and ask victims to pay a substantial ransom to retrieve data. However, there is no guarantee that once the ransom is paid the data will be decrypted.
There are three types of Malware and Ransomware in circulation:
1: Encrypting Ransomware
It’s designed to block system files and demand payment to provide the victim with the key that can decrypt the blocked content. Examples include Zepto, RAA, Crypto and more which are discussed below.
2: Locker Ransomware
Locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. The files are not encrypted in this case, but the cyber criminals still ask for a ransom to unlock the infected computer. Examples include Winlocker.
3: Master Boot Record ransomware (MBR)
Overwrites the master boot record (MBR) of the affected PCs, leaving their operating systems in an unbootable state. Examples include Satana and Petya Ransomware.
What is Petya Malware?
In 2017, the UK was subject to several Malware attacks such as the WannaCry virus that brought the NHS to a standstill in May 2017. Petya Malware crippled large businesses and it’s been reported that the virus source stemmed from a contaminated software update from MeDoc – a Ukrainian accountancy software firm.
Petya originally emerged in March 2016, but whilst the latest strain carries many similar properties, this new strain that’s since been renamed to “NotPetya” “Petna” and “GoldenEye” is proving even more powerful.
How far has Petya spread so far?
Petya has already infected thousands of computers on an international scale, with reported attacks in France, Germany the UK and America. However, the Ukraine was hit the hardest, with banks, Telecom operators and Government organisations becoming the latest victims.
How does Petya work?
The new strain of Petya differs from many other types of Malware and Ransomwares such as Zepto, Locky and RAA, due to the way in encrypts files. Designed to present in a way similar to WannaCry Ransomware, Petya is very different as it denies access to your entire system by encrypting files in the computer’s hard drive and also encrypts the MBR record on hard disks rendering the machines useless.
Petya also harvests usernames and passwords so the attackers could potentially gain access to infected systems even after they are restored.
How do you get Petya?
Petya embraces the EthernalBlue weakness in Microsoft Windows (a software vulnerability linked to the WannaCry attacks) to gain possession of PC’s and its data. Whilst many users have since installed the patch Microsoft released to resolve the security threat, some haven’t, and the minute Petya has sustained control of the computer it quickly takes over.
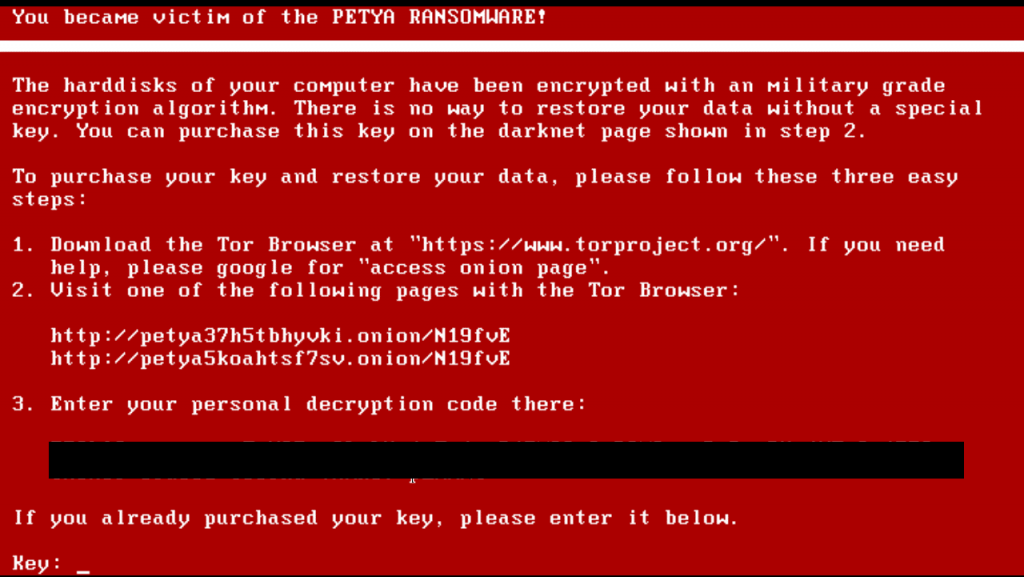
If you are a victim of Petya, you’ll see the below image displayed on your screen. The flashing screen showing a ASCII (American Standard Code for Information Interchange) page.
What is Locky Ransomware?
Locky Ransomware is a powerful virus, similar in many ways to the Petya, Rapid and WannaCry. It’s called Locky because this type of Ransomware renames all users important files giving them the extension .Locky.
However, Locky does more than just changing a victims file extensions. It corrupts all the files first so you can’t use them and demands a fixed fee (set out by cyber criminals) to decrypt them. This is often the only option to get your files back, however there is no guarantee that after the fee has been paid they will automatically be restored to their original state.
How do you get the Locky virus?
Computers without sufficient anti-virus that also provides Malware protection could be susceptible to Locky attacks.
The Locky virus is delivered in a email containing an attached document (Troj/DocDl-BCF). If you open the document, the words inside look all scrambled up (see below). The document advises you to enable macros “if the data encoding is incorrect.”.
If you enable macros, you don’t actually correct the text encoding (that’s a subterfuge); instead, you run code inside the document that saves a file to disk and runs it. The saved file (Troj/Ransom-CGX) serves as a downloader, which fetches the final malware payload from the cyber criminals.
The final payload could be anything, but in this case is usually the Locky Ransomware (Troj/Ransom-CGW). Locky then corrupts all files that match a long list of extensions, including videos, images, source code, and Microsoft Office files on your machine.
What types of files does Locky encrypt?
Your C: drive will probably be the first thing that’s encrypted, however Locky also corrupts files in any directory on any mounted drive that it can access. This includes removable drives that are plugged in at the time, or network shares that are accessible, including servers and other people’s computers and easily spreads across Windows, OS X and Linux platforms.
Locky can also spread from one device to another. If are logged in as an administrator and you get hit by Locky, it can easily spread to other users causing serious disruption to your business.
What is Zepto Ransomware?
As with all types of Malware and Ransomware viruses, RAA, Locky and Zepto Ransomware encrypt the users system files and demand a substantial fee to de-encrypt them. In the past three weeks, Infinity Group have had a lot of calls from frantic business professionals that have been targeted by Malware – some had even paid the ransom as a result of RAA, Locky and Zepto Ransomware attacks but never received any files back.
In February this year, Locky Ransomware emerged, this is the virus that encrypts your machine and renames all your files with .Locky extension. This was closely followed by RAA Ransomware last month that uses Javascript. However, this month we have been made aware of another new virus to enter the business world.
What is a Zepto File?
Zepto Ransomware is thought to be a variant of Locky and shares many of the same attributes; although this time a users files are all renamed with a .zepto file extension. In the first week of July 2016, experts observed more than 140,000 emails containing the Zepto Ransomware virus. As the attack gets more established these figures will dramatically rise. At present there are two main distribution methods for the Zepto Ransomware virus although others will likely emerge.
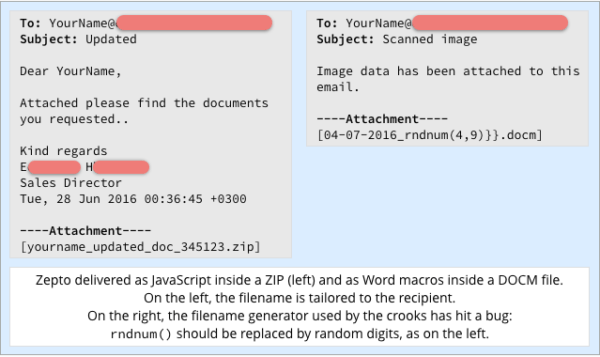
1: In emails with an attached ZIP file
If you are the recipient of the ZIP file, clicking on it will unzip a file with a Javascript extension. Opening the Javascript file will download the Zepto Ransomware virus as a .EXE file and run it on your machine.
2: In emails with an attached .DOCM file which is a macro enabled document file (see above right)
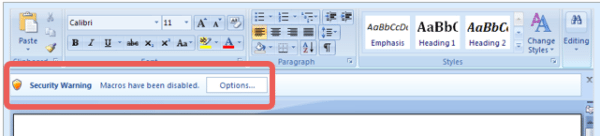
Double clicking the .DOCM file will open it in Microsoft Word. However the macro’s within the document won’t automatically run (thanks to an update by Microsoft a few years ago). However, the document will subtly prompt you to enable macros (see below image). So hopefully this will be the less invasive option for recipients out of the two – as most people are unlikely to click on the prompt.
The RAA Ransomware virus
RAA is a strain of Ransomware that was discovered by security researchers which is disguised as a document attached to an email that once opened automatically starts encrypting files. Unlike types of Malware and Ransomware viruses, RAA is coded entirely in Javascript; which increases its chances of being activated because Javascript documents don’t always trigger a security warning on some operating systems nor require administrator access to run.
If a user does open the RAA Ransomware file it will automatically encrypt all files and display a Russian ransom note on screen along with a set cost to restore all files. The only way to retrieve your files is to use a system backup or pay the fine to the hackers and keep your fingers crossed that you get your files back.
Here’s some useful tips to help protect your company from RAA ransomware attacks:
- We advise that awareness of the new RAA Ransomware is made public within companies so employees are aware of it and are wary of opening attachments especially with a .js extension.
- Ensure all company Antivirus software is active and kept up to date
- Windows can be programmed not to start the “Windows Based Script Host” when a .js file is double-clicked. We recommend this is implemented on all Windows machines.
- We also advise that macro enabled documents (such as .docm and .xlsm) are proceeded with great caution
What is Crypto Ransomware?
Its a form of encrypting Ransomware that’s described above. Crypto Ransomware encrypts files stored on the user’s computer or mobile device and in it’s simplest form, the encryption corrupts the contents of a file, so that it is unreadable by either the user or the device itself. To restore it for normal use, a decryption key is needed to decrypt the file.
How can I protect my business from Malware attacks?
In the first instance, we do not advise you pay the ransom set out by the cyber criminals. Infinity Group are Cyber Security Consultants and are able to help with emergency IT Support. instead get in touch with us to see if we can restore your files via backups. This is not something that is easily done as your machine(s) will be infected, however our IT Security Consultants have the knowledge of with several methods of undertaking this procedure.
Having a Backup and Disaster Recovery solution in place can help your organisation recover from a Malware attack and restore your business operations quickly and effectively. However, sometimes file retrieval is not possible due to the types of initial backup settings.
- How secure is your business setup?
- What antivirus software is in place and does it also prevent malware? (many don’t) Intercept X by Sophos is a brilliant way of protecting yourself from all the different types of Malware
- Do you have sufficient disaster recovery and backups in place?
- What security protection do you have in place for emails?
- Do you have a sufficient firewall in place?
Infinity Group are IT Security specialists and Cyber Security Consultants. If you would to find out more, please get in touch.



