Mobile Malware and mobile device security poses a range businesses threats, especially to those who favour Bring Your Own Device (BYOD) and remote working policies. In light of PC Malware viruses such as the Zepto and RAA Malware, many businesses remain unaware that there is also a large amount of mobile Malware in circulation.
What is Mobile Malware?
With the sudden growth in public Wi-Fi hotspots over the past few years’ cyber criminals are using these as another opportunity to carry out attacks. Cyber criminals can use insecure public Wi-Fi networks to inject Malware into the devices connected to it. The hackers use the Malware to gain access to a user’s entire device this includes email, files, passwords and photos. Many people who use public Wi-Fi hotspots use the same device they use for work – meaning they will have lots of business-related private information on their device. Hackers can intercept that information and then target that business.
One of the most prolific mobile Malware attacks to date was the Hummingbad Malware that earlier this year reportedly infected over 10m Android handsets worldwide. By attaching itself to infected versions of trusted Android apps, Hummingbad implemented applications to generate fraudulent advertising revenue, and collected personal data to sell on, whilst using up all the recipients data allowance.
For companies who embrace a BYOD policy, Enterprise Mobility Management (EMM) platforms can mitigate the risk of Malware and help protect corporate data. Meanwhile, robust security policies and mobile anti virus software can be installed on employee’s personal mobile devices without invading their personal privacy.
iOS and Android device usage for business
Mobile Apps present a security risk to businesses, as confidential company data is entrusted to a third party’s security protocols by default. Employees who use apps for work purposes, have to rely only on the strength of passwords they set for protection rather than robust end-to-end encryption. Whilst the major App Stores automatically scan for malicious apps, an employee can download a multitude of apps from third party App Stores that appear harmless but could potentially contain mobile Malware to infect the device and extract the data.
By creating a separate, corporate app store on employees devices through an Enterprise Mobility Management (EMM) platform, IT departments can easily ensure that only approved apps can access corporate information, whilst still giving employees the freedom to download whatever apps they wish for personal use
While Apple is said to have complete control over its iOS update system making it relatively secure, Malware does still exist for IOS. The StageFright attack in 2015, exploited weaknesses in the Android source code and allowed hackers to remotely execute malicious code. As Android has to rely on vendors to patch issues which is why we recommend all BYOD Android devices have anti virus software installed by the employer if they are to be used for work purposes.
It can be challenging to manage software updates on BYOD devices. However, enlightening employees who use Android devices aware of the above attack and encouraging them to ensure their personal device is up to date with the latest patches, will assist in helping overall mobile device security.
This blog explores the main points to consider that will help improve mobile device security and prevent mobile Malware threats – however there are many more things to also take into consideration. Mobile Device Management and Mobile Security are worthy of significant time and investment by any company even those who don’t embrace BYOD.
Why are Public Wi-Fi hotspots a threat to businesses?
During the summer of 2017, the Russian hacking group ‘Fancy Bears’ leaked documents exposing Ex-Premier League football players Dirk Kuyt, Carlos Tevez and Gabriel Heinze claiming they were cleared to use banned drugs at the 2010 World Cup. The leaked documents also claimed that over 160 players failed drugs tests in 2015. In response to this, and to avoid future interceptions, the Football Association (The FA) announced they are focusing heavily on cyber security for the World Cup 2018. All players will be banned from using public Wi-Fi hotspots at any time during the tournament, to alleviate any risk of sensitive information being hacked and leaked via use of public Wi-Fi hotspots.
It was published that security researcher Mathy Vanhoef of KU Leuven in Belgium discovered that Public Wi-Fi hotspots are being used to carry out attacks known as ‘Krack.’ Using a vulnerability in WPA2’s, another form of authentication that the host of the Wi-Fi hotspots use in order to encrypt the network. Worryingly, a huge amount of Wi-Fi enabled devices and networks use WPA2. It was then reported by Wired that a flaw in WPA2 could be exploited to steal data of those connected. In response, updates are urgently being rolled out in order to fix the issue. Microsoft were reported to roll out their patch this week. Below you can see a video example of how the ‘Krack’ attacks are carried out.
Unfortunately, ‘Krack’ attacks aren’t the only form of cyber-attacks that can be carried out on users of Public Wi-Fi hotspots. The updates that WPA2 isn’t going to stop cyber criminals being able to infiltrate unsecure Wi-Fi hotspots using different methods.
Public WiFi hotspots, pose a huge risk to all users especially business users. In the past, there has been a significant rise in the number of employees working outside of the office and using public Wi-Fi hotspots in places such as coffee shops, airports and hotels whilst working remotely via the Cloud. Although there are numerous business benefits of employees working remotely, it’s imperative that the correct security measures are in place to protect your businesses data.
Public Wi-Fi networks that do not require a password to join them, lack sufficient encryption and are likely insecure. This provides a great opportunity for cyber criminals to access and steal almost all information on a user’s mobile device. And, as the hacker sits in between the device and the public Wi-Fi it is connected to, the user remains unaware all their information (and potentially highly sensitive company data) is actually being extracted.
By educating employees of the dangers of using insecure public Wi-Fi businesses can help to mitigate potential threats and help avoid any unwanted attacks and data theft. It is also crucial that acceptable Wi-Fi usage outside the office environment is publicised to employees and enforced.
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle attack is carried out by cyber criminals exploiting a security flaw in the unencrypted public Wi-Fi router, they scan the data between the router and connected devices. The attacker will target a user of the public Wi-Fi hotspot that is in communication with someone outside of the public Wi-Fi hotspot e.g. a colleague in the office. They can then intercept communication between those two people and any personal data being sent. This form of attack can often go undetected. Man-in-the-Middle attacks can occur on any type of device including mobiles and tablets.
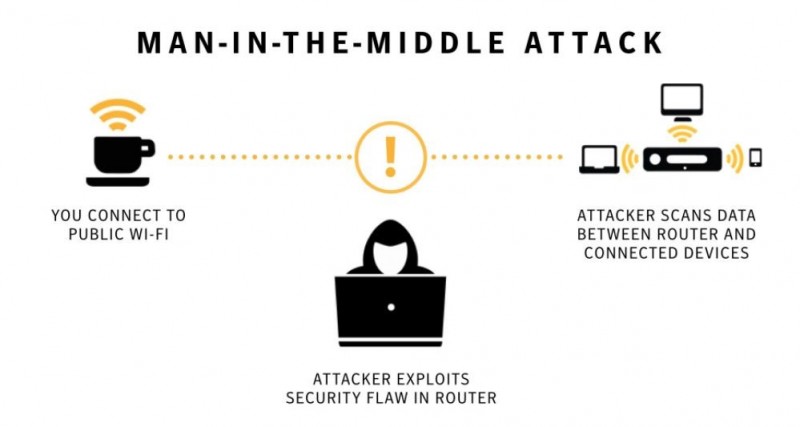
How can you protect your business when using Public Wi-Fi?
- Use VPN’s (Virtual Private Network) VPN’S encrypt your internet connection to ensure your connection is secure and protects your privacy – make sure all employees working remotely are set up with a VPN and they use this when out of the office.
- Use HTTPS when visiting websites – HTTP isn’t encrypted therefore you’re vulnerable when visiting HTTP sites. HTTPS websites are encrypted making them secure. Below is an example of a secure website on both a computer and mobile.
- Use endpoint protection – Ensure you have industry standard security protection on your device. Intercept X by Sophos is a great way to protect your device from malware that could be transmitted via a public Wi-Fi hotspot.
- Microsoft Enterprise Mobility Suite + Security – InTune, an application within Microsoft Enterprise Mobility Suite enables you to turn off automatic connections to public Wi-Fi hotspots. This ensures employees only connect to selected hotspots and prevents employees accessing unencrypted networks on their business devices.
- Secure your login credentials – Use two-factor authentication for all login credentials on accounts.
Why should businesses consider a BYOD Policy?
Many businesses are now choosing to drastically reduce their investments in corporate devices and support a Bring Your Own Device (BYOD) arrangement instead. Despite the heightened security risks that BYOD poses to corporate network security, sensitive data and access to company files, the global trend continues to grow at a rapid pace.
BYOD is typically adopted by businesses to reduce device and usage costs but also to improve employee productivity and general morale, as employees prefer to use devices they are familiar with. As BYOD policies are now commonplace in the majority of business it is important to also include Mobile device security within your Enterprise Mobility Management strategy.
Effective BYOD Management and Security
Effective management is key not only to monitor staff performance but to maintain a sufficient level of IT Security and compliance. The key for a happy balance between employees’ wants and IT Security management is two-way agreement that addresses each party’s concerns. Businesses that support BYOD should have a BYOD Acceptable User Policy (AUP) implemented to provide guidance to employees about acceptable use of their own devices for work purposes and guidance on how to process corporate and personal data.
Whilst devices are personally owned by employees not the business there are a few steps businesses can enforce to ensure each device complies with your AUP. This ensures that if a device is lost or stolen, hacked or the employee leaves there is a reasonable level of security protection in place.
The Information Commissioners Office (ICO) recommends that within the BYOD policy businesses specify that:
- Devices are auto locked with a strong password
- Devices use encryption to store data on the device securely
- Devices have antivirus software installed on personal devices
- Businesses maintain a clear separation between the employee’s private and work data, for example, by only using apps which you have approved for business use and use separate apps for personal use.
- Businesses provide additional technical support to the employees on their personal devices when they are used for business purposes
- Businesses make clear to employees that they can only process corporate personal data for corporate purposes
To address the data protection and security breach risks, the ICO guidance also strongly recommends businesses specify the following:
- Which type of corporate data can be processed on personal devices
- How to encrypt and secure access to the corporate data
- How the corporate data should be stored on the personal devices
- How and when the corporate data should be deleted from the personal devices
- How the data should be transferred from the personal device to the company servers
Infinity Group are Microsoft Gold Partners or if you wish to speak to one of our IT Consultants regarding the device or IT Security, please get in touch.
