The words ‘data breach’ are enough to send shivers down any business leaders’ spine. If you leak customer data, even if accidentally, it can result in significant financial fines, reputational damage and a whole lot of stress.
One of the most significant data breaches in recently years was the PDL data breach. It affected 1.2 billion records and is still spoken about today as an example of what you don’t want to happen to your business. Below, we explore how the PDL data breach occurred and the important lessons to take away for your business data.
The PDL Data breach: an overview
The PDL data breach was first discovered by security researchers, Vinnie Troia and Bob Diachenko, in October 2019. 1.2 billion personal data records (totalling 4.2 terabytes) were freely accessible via an insecure server on the dark web. People Data Labs (PDL) were traced as the source of part of this data set.
Although the server was not owned by PDL, it is believed that a customer failed to properly secure the database. The exposed information included a wide range of personal details, raising concerns about the potential misuse of this data for criminal activities such as phishing, scamming and identity theft.What data was leaked in the PDL breach?
The PDL data breach shared data records included usernames, social media accounts, 622 million email addresses and 50 million unique phone numbers. Whilst the data set did not contain passwords or social security numbers, it did have all the information necessary to impersonate someone.
Vincent Troia, who found the breach, stated at the time: “This is the first time I’ve seen all these social media profiles collected and merged with user profile information into a single database on this scale. From the perspective of an attacker, if the goal is to impersonate people or hijack their accounts, you have names, phone numbers, and associated account URLs. That’s a lot of information in one place to get you started.”
The intention of the data leak remains unclear, because this data was fully accessible with no payment required and with no links to an author. PDL has since claimed that the data was not obtained as a result of a breach, but instead was likely resold or released by one of their customers.
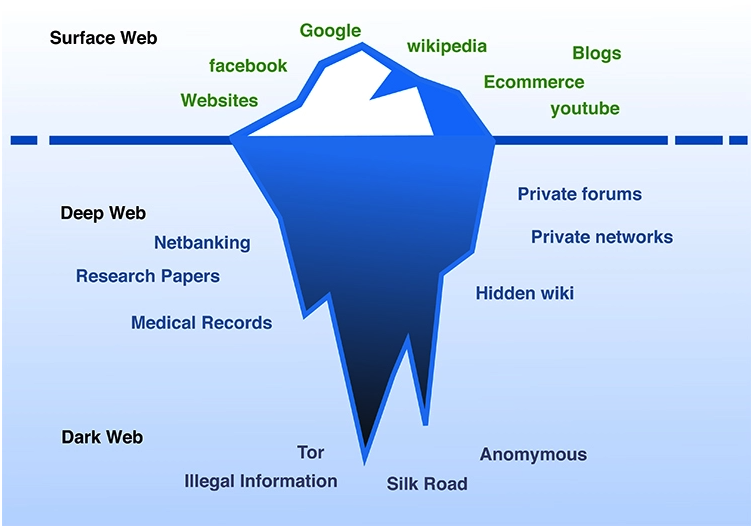
What was the role of the deep web and the dark web?
The unsecured server containing the massive dataset in this breach was likely hosted on the deep web. The deep web is an area that is not accessible by the main stream search engines where you can often find leaked data.
The deep web was initially designed for the US secret service, so that they could access files without being detected. Unfortunately it has turned out to be a double-edged sword as the very feature of un-traceability which was invaluable to the military became used by criminals. Although the PDL particular data set has since been removed by the FBI, the researchers have no way of knowing if anyone accessed the data set prior to its removal.
After the breach was discovered, the dark web became a potential marketplace for the data. The dark web is a website within the deep web that is linked to illegal activity. Cyber criminals could have sought to sell or distribute the compromised information within dark web forums and marketplaces, further jeopardising the privacy of the affected individuals.
While it’s unclear if the data was actively traded on the dark web in this specific case, it remains a common scenario in data breaches. This is where businesses risk losing sensitive IP or placing their customers at risk.
How common is a data breach?
It may be tempting to think the PDL data breach is a one-off scenario. But it’s far from it.
Leaks like the PDL one are commonplace and they have existed since the internet was created. In 2024, more than 5.5 billion data breaches occurred globally.
And the individual leaks are growing. Troy Hunt, who runs data tracking exposure service ‘HaveIBeenPwned’ observed that we are seeing more data than ever being circulated, from both new breaches and duplication of previous breaches.
There are a number of factors driving the rise in data breaches including:
- Increased digitisation. As more aspects of our lives move online, the amount of data stored digitally has exploded. This creates a larger target for cyber criminals.
- Sophistication of cyber attacks. Hackers are constantly developing new and more sophisticated methods to breach security systems. This includes malware, phishing, ransomware and social engineering tactics.
- Human error. Employees can make mistakes that lead to data breaches, such as clicking on phishing links, using weak passwords or misconfiguring systems. Phishing scams are becoming more common too, as criminals use AI to exacerbate their efforts.
- Lack of security investment. Some organisations fail to invest adequately in cyber security measures, leaving them vulnerable to attacks. This can be due to budget constraints, lack of awareness or complacency.
- Value of data. Personal data has become a valuable commodity, with cyber criminals seeking to steal and sell it for financial gain. This motivates them to target organisations that hold large amounts of sensitive information.
- Expanding attack surface. With the rise of cloud computing, mobile devices and IoT devices, the number of entry points for cyberattacks has increased significantly. This makes it more challenging to secure systems.
- Regulatory landscape. While regulations like GDPR aim to protect personal data, they also increase the pressure on organisations to report breaches, making them more visible.
How to prevent data breaches in your business
A data breach can bring substantial damage to your business. If you want to reduce the risk, here are our tips to follow:
- Implement strong security measures. This includes using firewalls, intrusion detection systems and antivirus software to protect against malware and other threats.
- Encrypt sensitive data. Encryption makes data unreadable to unauthorised individuals, even if they manage to access it. A good business system should encrypt data for you.
- Use multi-factor authentication. This adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a code sent to their phone.
- Conduct regular security audits. Audits can help identify vulnerabilities in a business’s security systems and ensure that they are addressed.
- Comply with data privacy regulations. Regulations such as GDPR and CCPA impose strict requirements on how businesses collect, store, and use personal data.
By taking these steps, businesses can significantly reduce their risk of being affected by a data breach. However, it is important to remember that no security system is perfect. Businesses should always be prepared to respond to a breach if one occurs. Aim to craft a robust incident response plan that details how you’ll react and who is responsible for specific actions. This will ensure a swift resolution.
If you want to learn more about how to protect your data and minimise risk across your business, we’ve put together insights from leading cyber security experts into a digestible video series. Our Get to Secure series will teach you everything you need to keep your business safe, even as the threat level rises.
Access it for free below.



