Organisations of all sizes, globally have fallen victim to harmful cyber attacks such as WannaCry, Petya and Locky, which have shut down entire systems and held their data for ransom. There are increasingly a huge rise in cyber attacks, and cyber criminals are now working harder to devise new ways of harvesting businesses data, bank details and any other form of sensitive information.
With the GDPR now in affect and cyber crime on a continuous increase, it’s important that businesses are fully aware of the different types of cyber threats and the ways they are delivered. Alongside Malware, we have seen a significant rise in typosquatting attacks using cloned Doppelganger Domains. These are domains very similar to the existing domain name of a company. Alongside these ‘fake’ domains, ‘fake’ email domain extensions are also activated. The success rate of this type of cyber crime is high as it relies on simple human error, as emails received from the almost identical domain are easily mistaken as genuine. There is two different ways that cyber criminals are using these domains.
What are Doppelganger Domains?
Doppelganger Domains are clones of legitimate domains but with a very slight difference, for example if a company email domain extension was @infinity.group.co.uk, cyber criminals could set up another very similar domain such as www.infinitygroup.co.uk (without the dot) and could use this email domain extension to individually target the customers of our business using @infinitygroup.co.uk. With the dot removed, it’s then easily mistaken by the recipient (such as a customer) as a genuine email from the company and is highly likely to be responded to.

Photo credit – https://www.wired.com
Emails being sent by mistake to Doppleganger Domains
Imagine this scenario.
One of our employees is in a rush and emails a colleague by typing in employeename@infinitygrou.co.uk missing the ‘p’, in most cases the sender will be notified with an undeliverable notification. However, if www.infinitygrou.co.uk is an owned domain, the email will then be received by someone it is not intended for and the sender will remain unaware.
Should a cyber criminal own that domain missing the ‘p’, they would receive that email and then be aware of the business email format which they can then use to gain more names. EG. Finding out who else works at the company by looking on LinkedIn. They can then target several users by email with a link to a related Malware.
Email fraud
The second technique is using a ‘catch all’ method. The cyber criminals wait for an email to be sent to the fraudulent domain eg. it could be a domain name very similar to a well-known bank or large organisation. As an example, www.’insertbrandname’bank.co.uk capturing all emails sent here eg. customer service@’insertbrandname’bank.co.uk that some people will likely send emails too.
At this point, the cyber criminals have access to a vast amount of email address’ and can quickly reply. The reply email a customer receives will appear highly genuine as all the information is present due to the intercepted email content being included. Cyber criminals can then engage in a seemingly innocent conversation with the customer and request confidential details which is how email fraud is performed.
Below you can see an image example – posing as Vodafone and asking you to view your bill, if you look the email is slightly different.
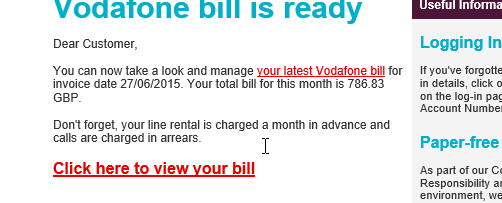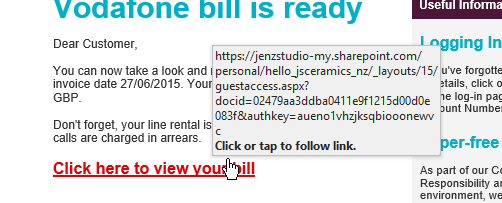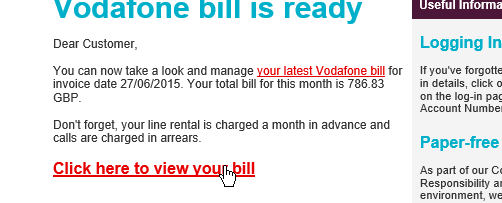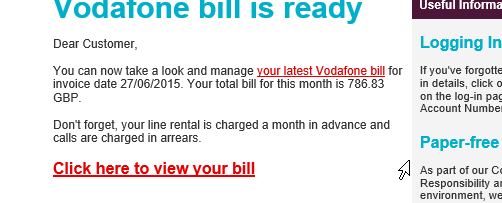
How easy is it to become a victim to email cyber attacks?
Whilst you may consider either method of attack highly unlikely, Godai Group carried out an experiment where they set up Doppelganger Domains for many fortune 500 companies and collected emails sent to mistyped domains. The outcome was staggering, over a period of six months, they managed to collect over 120,000 individual emails which contained a large amount of sensitive information such as business invoices, personal information, usernames and passwords etc.
A recent example, earlier this month the Consumer Credit reporting giant – Equifax were hit by a cyber attack which hacked in to their servers. 143 million people’s personal information was stolen. (Source – The BBC)
Soon after the cyber attack Equifax made a simple but detrimental mistake – at a time where their reputation and the security of the business was highly questionable by customers . Writing back to a possible victim on a Twitter post, Equifax directed them and three others to the web domain – securityequifax2017.com instead of equifaxsecurity2017.com. The website that Equifax directed the users to wasn’t a legitimate Website and had no connection with Equifax. The Web domain was a fake phishing website. Although Equifax deleted this tweet once another user on Twitter pointed out it was incorrect; it was live for 24 hours which is a a lot of time for users to have gone to the website and handed over their personal information to Cyber Criminals. (Source – The Verge).
When trying to access securityequifax2017.com now the screen below is displayed by Google.
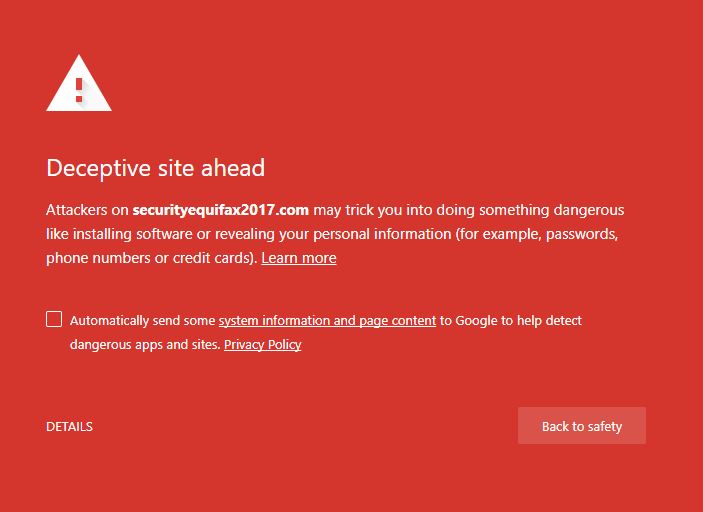
It’s clear that even the biggest businesses, despite having strong security set up, could potentially fall victim to doppelganger and typosquatting cyber attacks. These methods of attack are the easy option as unlike other types of cyber crime, criminals don’t need to try and bypass a system or break through any security measures to quickly gain information.
How can you protect your business?
As doppelganger and typosquatting attacks rely entirely human error, it’s very hard to come up with a definite solution to combat them. However, there are many things your business can do to reduce the chances.
- Staff awareness and training – With the GDPR now in play, data breaches now carry a high penalty. Make all staff aware of typosquatting email attacks so they know to look at the sender’s details before responding.
- Be extra vigilant – Look in your sent box regularly and check who you’ve sent emails too. Especially emails you need to manually type such as those not in your current address book. If you receive a typosquatting email, please alert the real company it’s in relation to so they are made aware.
- Use endpoint protection for devices – Ensure that all employees have an industry standard security protection put in place. Intercept X by Sophos is a fantastic way to protect your devices from malware and other security threats but cannot fully protect against Doppelganger Domains. If you are a well-known brand, purchase other close variants of your domain name to prevent these being brought by criminals.
- Back up – Ensure your business has robust back up and disaster recovery plan in place in the event of an attack.
Infinity Group are IT Security specialists and GDPR Consultants. If you are interested in implementing an IT Security strategy, please get in touch
